mirror of
https://github.com/nextcloud/all-in-one.git
synced 2025-12-20 06:26:57 +00:00
Merge pull request #2387 from nextcloud/enh/noid/add-further-details
add a details tag to note down more included features
This commit is contained in:
commit
cb5bee70b0
2 changed files with 60 additions and 3 deletions
61
readme.md
61
readme.md
|
|
@ -5,11 +5,68 @@ Included are:
|
|||
- Nextcloud
|
||||
- Nextcloud Office
|
||||
- High performance backend for Nextcloud Files
|
||||
- High performance backend for Nextcloud Talk
|
||||
- High performance backend for Nextcloud Talk and TURN-server
|
||||
- Backup solution (based on [BorgBackup](https://github.com/borgbackup/borg#what-is-borgbackup))
|
||||
- Imaginary (for previews of heic, heif, illustrator, pdf, svg, tiff and webp)
|
||||
- ClamAV (Antivirus backend for Nextcloud)
|
||||
- Fulltextsearch
|
||||
<details><summary>And more</summary>
|
||||
|
||||
- Simple web interface included that enables easy installation and maintenance
|
||||
- [Easy updates included](https://github.com/nextcloud/all-in-one#how-to-update-the-containers)
|
||||
- Update and backup notifications included
|
||||
- Daily backups can get enabled from the AIO interface which also allows to update all containers, Nextcloud and Nextcloud apps afterwards automatically
|
||||
- Instance restore from backup archive via the AIO interface included (you only need the archive and the password in order to restore the whole instance on a new AIO instance)
|
||||
- APCU as local cache
|
||||
- Redis as distributed cache and for file locking
|
||||
- Postgresql as database
|
||||
- PHP-FPM with performance-optimized config
|
||||
- A+ security in Nextcloud security scan
|
||||
- Ready to be used behind existing [Reverse proxies](https://github.com/nextcloud/all-in-one/blob/main/reverse-proxy.md)
|
||||
- Can be used behind [Cloudflare Tunnel](https://github.com/nextcloud/all-in-one#how-to-run-nextcloud-behind-a-cloudflare-tunnel)
|
||||
- Ready for big file uploads up to 10 GB, [adjustable](https://github.com/nextcloud/all-in-one#how-to-adjust-the-upload-limit-for-nextcloud)
|
||||
- PHP and web server timeouts set to 3600s, [adjustable](https://github.com/nextcloud/all-in-one#how-to-adjust-the-max-execution-time-for-nextcloud) (important for big file uploads)
|
||||
- Defaults to a max of 512 MB RAM per PHP process, [adjustable](https://github.com/nextcloud/all-in-one#how-to-adjust-the-php-memory-limit-for-nextcloud)
|
||||
- Automatic TLS included (by using Let's Encrypt)
|
||||
- HTTP/2 and HTTP/3 enabled
|
||||
- Only one domain and not multiple domains are required for everything to work (usually you would need to have one domain for each service which is much more complex)
|
||||
- [Adjustable location](https://github.com/nextcloud/all-in-one#how-to-change-the-default-location-of-nextclouds-datadir) of Nextcloud's datadir (e.g. good for easy file-sharing with host system on Windows and MacOS)
|
||||
- By default confined (good for security) but can [allow access to additional storages](https://github.com/nextcloud/all-in-one#how-to-allow-the-nextcloud-container-to-access-directories-on-the-host) in order to enable the usage of the local external storage feature
|
||||
- Possibility included to [adjust default installed Nextcloud apps](https://github.com/nextcloud/all-in-one#how-to-change-the-nextcloud-apps-that-are-installed-on-the-first-startup)
|
||||
- `ffmpeg`, `smbclient` and `nodejs` are included by default
|
||||
- Possibility included to [permanently add additional OS packages into the Nextcloud container](https://github.com/nextcloud/all-in-one#how-to-change-the-nextcloud-apps-that-are-installed-on-the-first-startup) without having to build your own Docker image
|
||||
- Possibility included to [permanently add additional PHP extensions into the Nextcloud container](https://github.com/nextcloud/all-in-one#how-to-add-php-extensions-permanently-to-the-nextcloud-container) without having to build your own Docker image
|
||||
- Possibility included to [pass the needed device for hardware transcoding](https://github.com/nextcloud/all-in-one#how-to-enable-hardware-transcoding-for-nextcloud) to the Nextcloud containe
|
||||
- Possibility included to [store all docker related files on a separate drive](https://github.com/nextcloud/all-in-one#how-to-store-the-filesinstallation-on-a-separate-drive)
|
||||
- [Fail2Ban can be added](https://github.com/nextcloud/all-in-one#fail2ban)
|
||||
- [phpMyAdmin, Adminer or pgAdmin can be added](https://github.com/nextcloud/all-in-one#phpmyadmin-adminer-or-pgadmin)
|
||||
- [Mail server can be added](https://github.com/nextcloud/all-in-one#mail-server)
|
||||
- Nextcloud can be [accessed locally via the domain](https://github.com/nextcloud/all-in-one#how-can-i-access-nextcloud-locally)
|
||||
- Can [be installed locally](https://github.com/nextcloud/all-in-one/blob/main/local-instance.md) (if you don't want or cannot make the instance publicly reachable)
|
||||
- [IPv6-ready](https://github.com/nextcloud/all-in-one/blob/main/docker-ipv6-support.md)
|
||||
- Can be used with [Docker rootles](https://github.com/nextcloud/all-in-one/blob/main/docker-rootless.md) (good for additional security)
|
||||
- Runs on all platforms Docker supports (e.g. also on Windows and Macos)
|
||||
- Included containers easy to debug by having the possibility to check their logs directly from the AIO interface
|
||||
- [Docker-compose ready](https://github.com/nextcloud/all-in-one/blob/main/docker-compose.yml)
|
||||
- Can be installed [without a container having access to the docker socket](https://github.com/nextcloud/all-in-one/tree/main/manual-install)
|
||||
- Can be installed with [Docker Swarm](https://github.com/nextcloud/all-in-one#can-i-run-this-with-docker-swarm)
|
||||
- Can be installed with [Kubernetes](https://github.com/nextcloud/all-in-one/tree/main/nextcloud-aio-helm-chart)
|
||||
- Almost all included containers Alpine Linux based (good for security and size)
|
||||
- Many of the included containers run as non-root user (good for security)
|
||||
- Included containers run in its own docker network (good for security) and only really necessary ports are exposed on the host
|
||||
- [Multiple instances on one server](https://github.com/nextcloud/all-in-one/blob/main/multiple-instances.md) are doable without having to deal with VMs
|
||||
- Adjustable backup path from the AIO interface (good to put the backups e.g. on a different drive)
|
||||
- Possibility included to also back up external Docker Volumes or Host paths (can be used for host backups)
|
||||
- Borg backup can be completely managed from the AIO interface, including backup creation, backup restore, backup integrity check and integrity-repair
|
||||
- [Remote backups](https://github.com/nextcloud/all-in-one#are-remote-borg-backups-supported) are indirectly possible
|
||||
- Updates and backups can be [run from an external script](https://github.com/nextcloud/all-in-one#how-to-stopstartupdate-containers-or-trigger-the-daily-backup-from-a-script-externally)
|
||||
|
||||
</details>
|
||||
|
||||
## Screenshots
|
||||
| First setup | After installation |
|
||||
|---|---|
|
||||
| 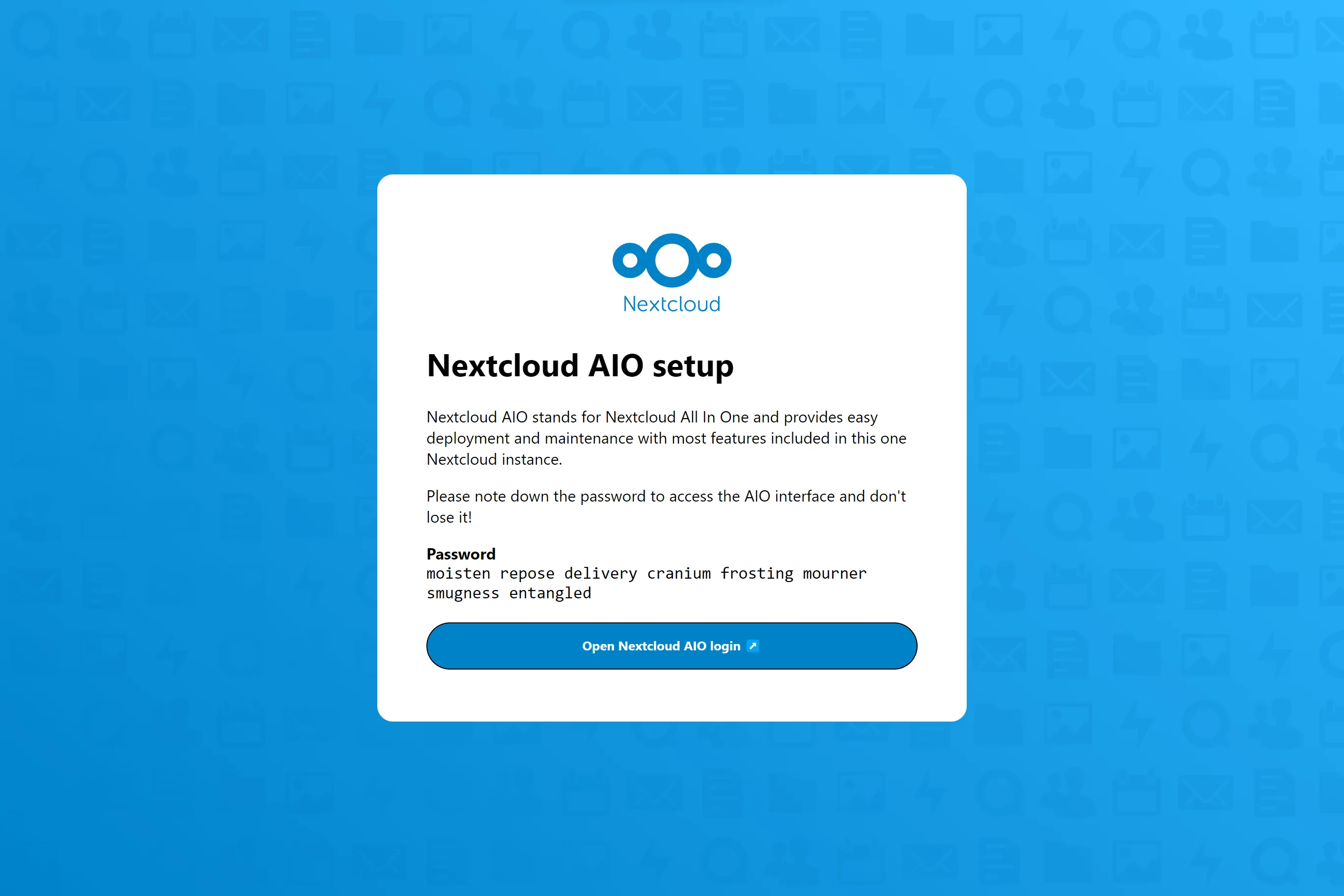 | 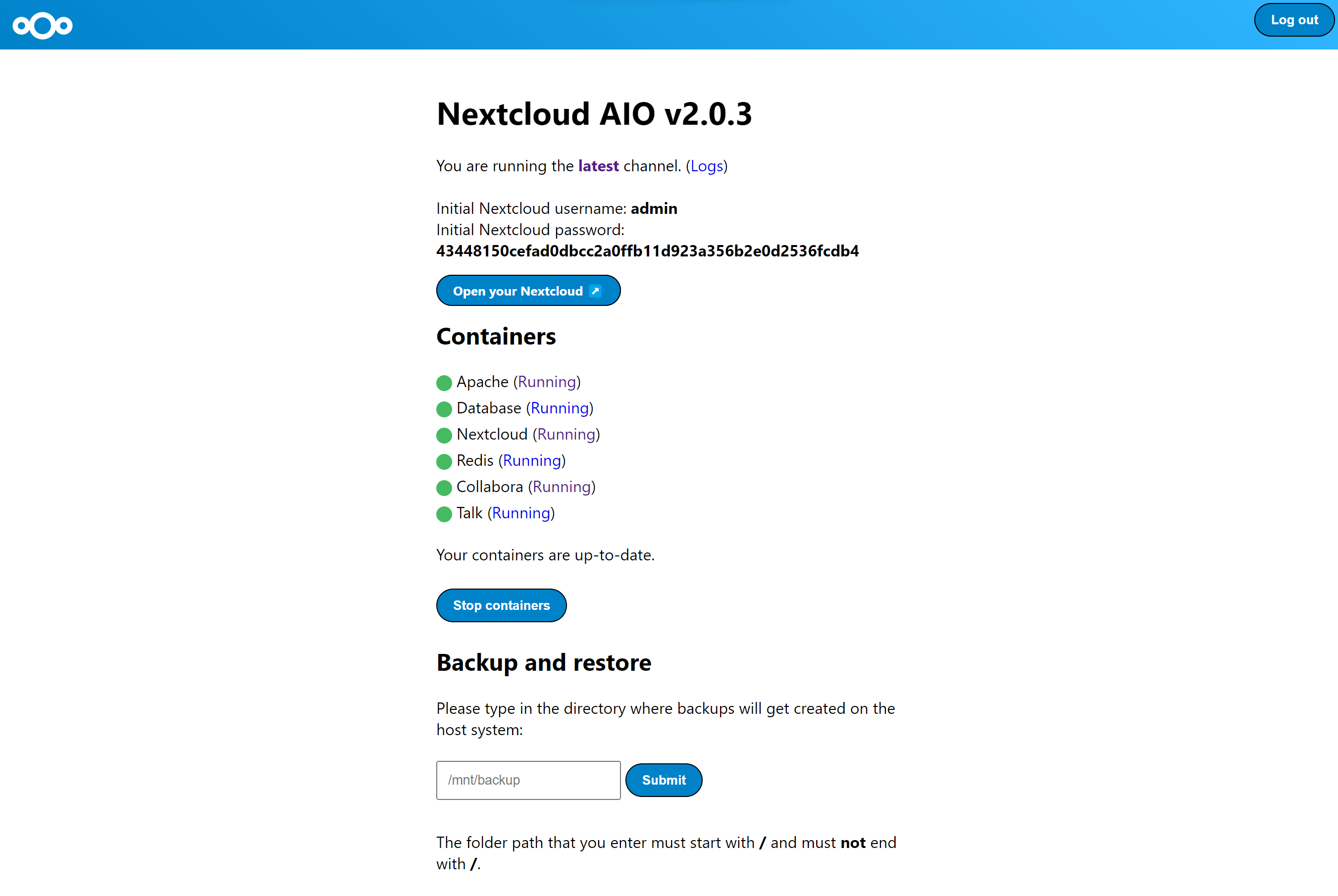 |
|
||||
|
||||
## How to use this?
|
||||
The following instructions are meant for installations without a web server or reverse proxy (like Apache, Nginx and else) already being in place. If you want to run AIO behind a web server or reverse proxy (like Apache, Nginx and else), see the [reverse proxy documentation](https://github.com/nextcloud/all-in-one/blob/main/reverse-proxy.md). Also, the instructions below are especially meant for Linux. For macOS see [this](#how-to-run-aio-on-macos), for Windows see [this](#how-to-run-aio-on-windows) and for Synology see [this](#how-to-run-aio-on-synology-dsm).
|
||||
|
|
@ -138,7 +195,7 @@ The easiest way to run it with Portainer on Linux is to use Portainer's stacks f
|
|||
- If you are using AIO's built-in Reverse Proxy and don't use your own, then may the certificate issuing possibly not work out-of-the-box because Cloudflare might block the attempt. In that case you need to disable the Proxy feature at least temporarily in order to make it work. See https://github.com/nextcloud/all-in-one/discussions/1101.
|
||||
|
||||
### How to run Nextcloud behind a Cloudflare Tunnel?
|
||||
Although it does not seems like it is the case but from AIO perspective a Cloudflare Tunnel works like a reverse proxy. So please follow the [reverse proxy documentation](./reverse-proxy.md) where is documented how to make it run behind a Cloudflare Tunnel. Also see https://github.com/dani-garcia/vaultwarden/wiki/Running-a-private-vaultwarden-instance-with-Let%27s-Encrypt-certs#cloudflare-setup for additional docs on this topic.
|
||||
Although it does not seems like it is the case but from AIO perspective a Cloudflare Tunnel works like a reverse proxy. So please follow the [reverse proxy documentation](./reverse-proxy.md) where is documented how to make it run behind a Cloudflare Tunnel. However please see the [caveats](https://github.com/nextcloud/all-in-one#notes-on-cloudflare-proxytunnel) before proceeding.
|
||||
|
||||
### Disrecommended VPS providers
|
||||
- Stratos VPS crash/freeze/make errors when they reach an extremely low PID limit, which is very quickly reached by AIO, see [here](https://github.com/nextcloud/all-in-one/discussions/1747#discussioncomment-4716164), Strato does normally not increase this limit.
|
||||
|
|
|
|||
|
|
@ -138,7 +138,7 @@ You can get AIO running using the ACME DNS-challenge. Here is how to do it.
|
|||
|
||||
<summary>click here to expand</summary>
|
||||
|
||||
Although it does not seems like it is the case but from AIO perspective a Cloudflare Tunnel works like a reverse proxy. Here is how to make it work:
|
||||
Although it does not seems like it is the case but from AIO perspective a Cloudflare Tunnel works like a reverse proxy. Please see the [caveats](https://github.com/nextcloud/all-in-one#notes-on-cloudflare-proxytunnel) before proceeding. Here is then how to make it work:
|
||||
|
||||
1. Install the Cloudflare Tunnel on the same machine where AIO will be running on and point the Tunnel with the domain that you want to use for AIO to `http://localhost:11000`. ***If the Tunnel is running on a different machine, you can alternatively instead of `localhost` use the private ip-address of the host that is running the docker daemon. If you are not sure how to retrieve that, you can run: `ip a | grep "scope global" | head -1 | awk '{print $2}' | sed 's|/.*||'`. If the command returns a public ip-address, use `ip a | grep "scope global" | grep docker0 | awk '{print $2}' | sed 's|/.*||'` instead (the commands only work on Linux)***
|
||||
1. Now continue with [point 2](#2-use-this-startup-command) but additionally, add `--env SKIP_DOMAIN_VALIDATION=true` to the docker run command which will disable the dommain validation (because it is known that the domain validation will not work behind a Cloudflare Tunnel). So you need to ensure yourself that you've configured everything correctly.
|
||||
|
|
|
|||
Loading…
Add table
Add a link
Reference in a new issue